World's first AIto ace hacking exams
Why Teams Choose Shinobi
See the dramatic improvements teams achieve when they switch to AI-powered penetration testing
Accuracy Improvement
99% Accurate
findings
Testing Speed
10x Faster
test completion time
Human Level Creativity
100x More
than vulnerability scanners
Transform Your Security Testing Today
Join innovative teams who've already made the switch to faster, more accurate penetration testing with Shinobi AI.
Continuous Pentesting for the AI Era
Always On. Always One Step Ahead.
Intelligent Testing on-demand
Catch critical bugs early
IDOR on user API exposes IoT and smart vehicle network's Super Admin
Broken Access in Bookings exposes Parents and Children's data
Privilege Escalation leads to Charging Station takeover
Missing X-Frame-Options and CSP on marketing pages enables clickjacking
Weak password policy allows short dictionary passwords
Get Tailored reports

How Shinobi Works
Experience the future of penetration testing with our AI-driven methodology. From intelligent scoping to actionable reporting, see how Shinobi transforms traditional security testing.
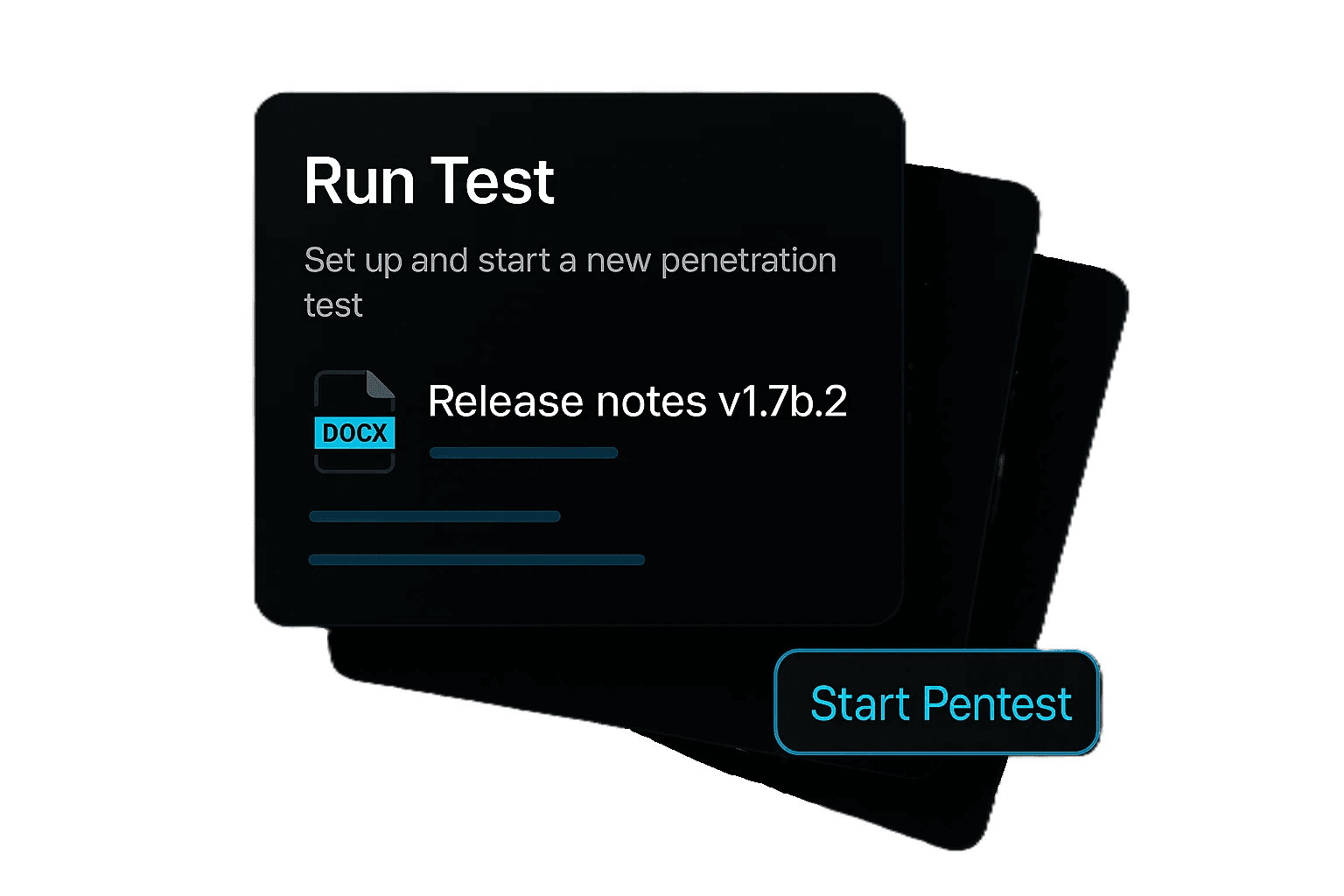
Scoping
Shinobi works like a human pentester - it starts with your defined scope of work. AI agents test only the apps, APIs, or mobile apps you authorize, with guardrails that prevent any out-of-scope activity. It also natively supports MFA and complex authentication flows, without scripts or extra setup.
Key Capabilities:
Web app, API, and mobile app testing
Intelligent in-scope guardrails
Native MFA and complex authentication handling
Zero scripting or configuration required
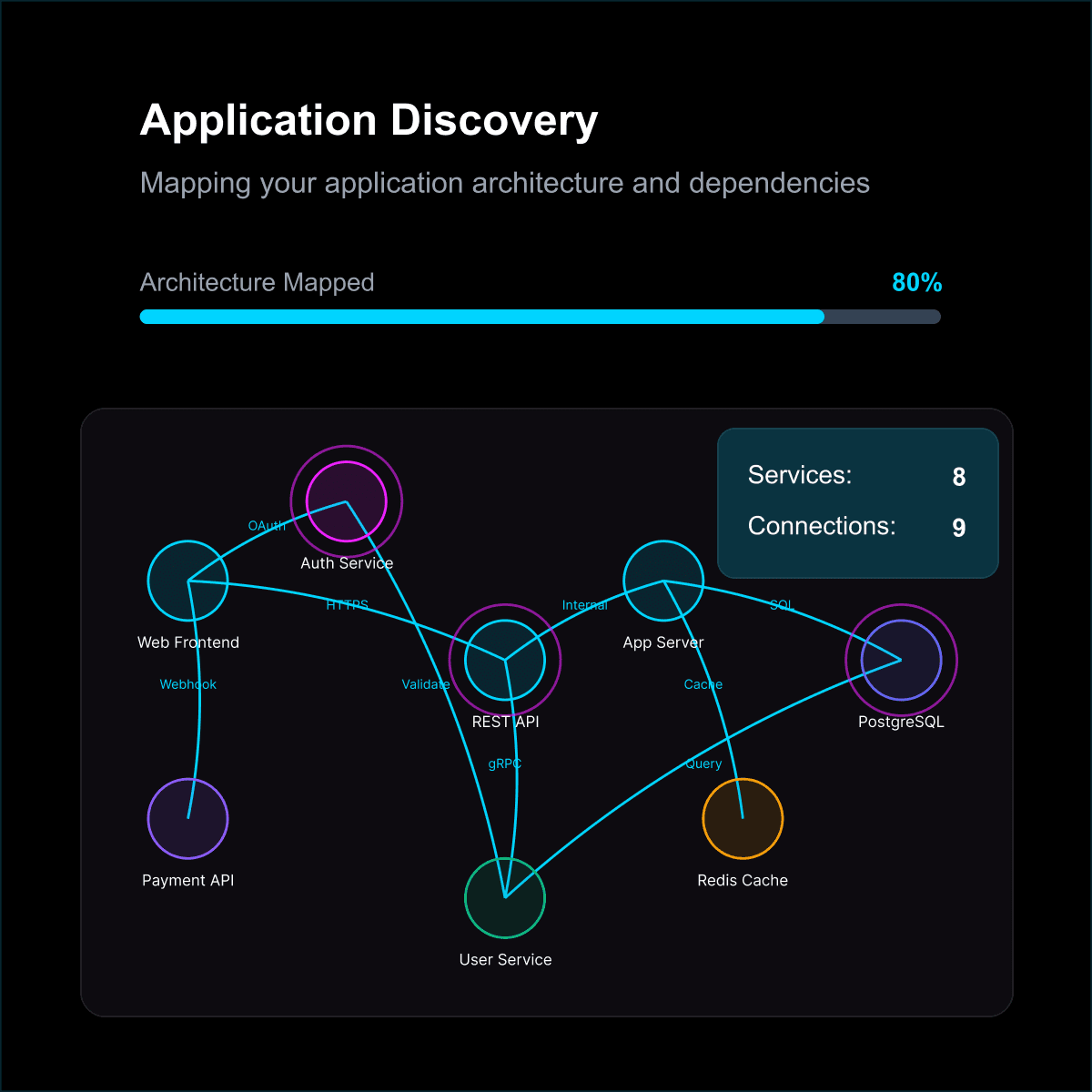
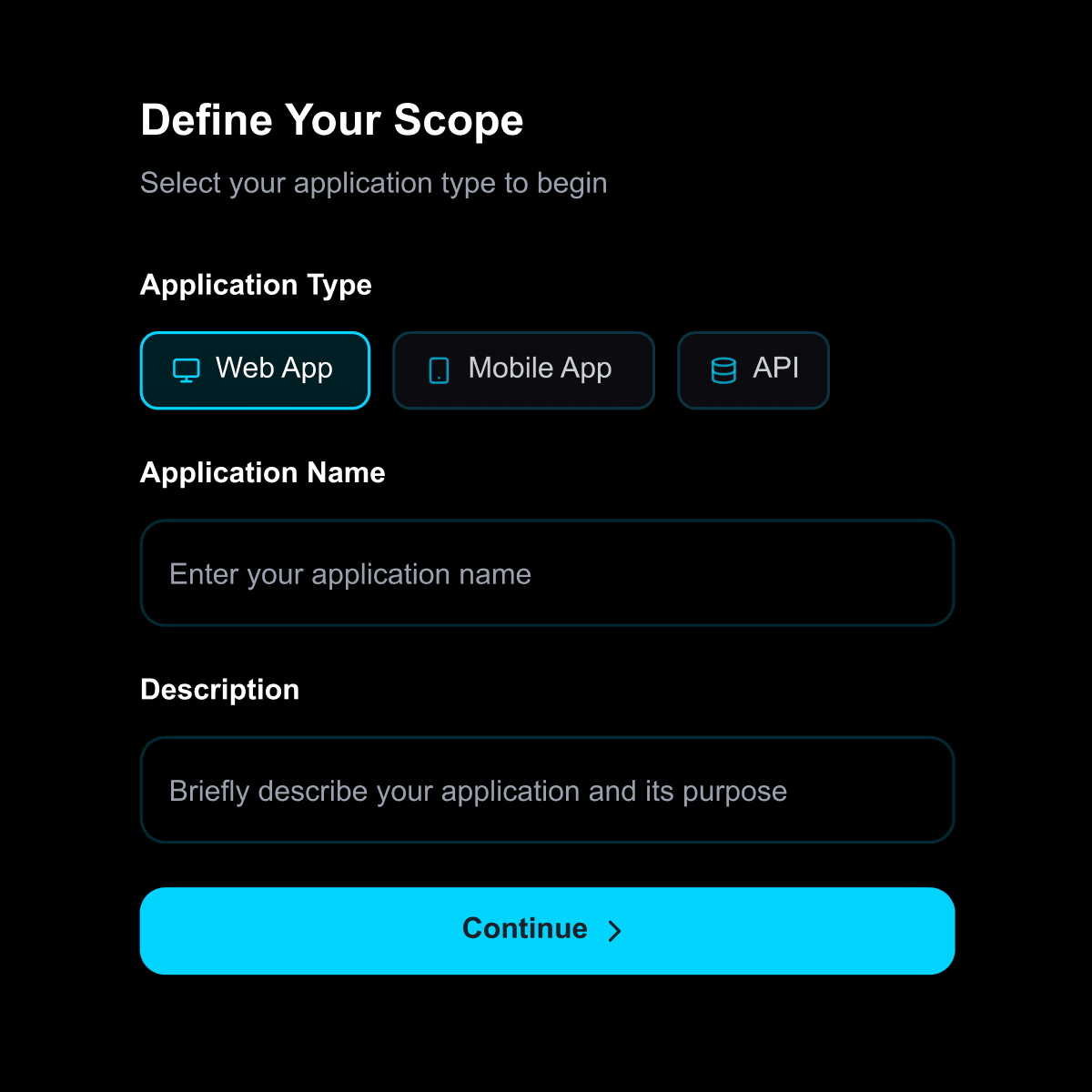
Reconnaissance & Discovery
Advanced reconnaissance combines active application mapping with context building. Shinobi crawls applications, identifies technologies, and researches tactics and techniques to build a comprehensive attack model
Key Capabilities:
Application endpoint and workflow mapping
Context Development
Technology stack identification
Attack modelling
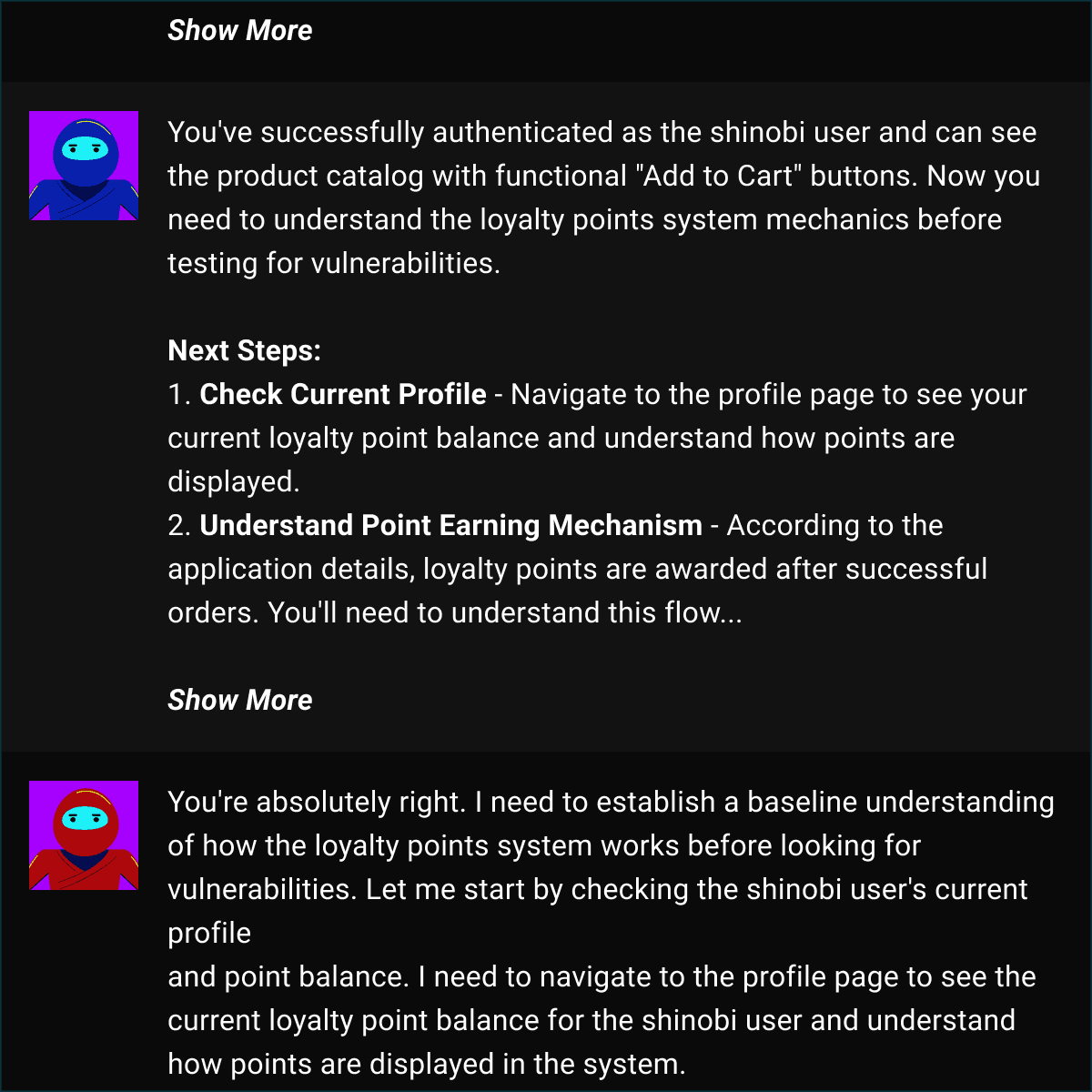
Testing
The core testing phase uses AI reasoning to generate sophisticated attack payloads and discover complex vulnerability chains. Unlike traditional scanners, Shinobi adapts its approach based on application responses and validates each finding.
Key Capabilities:
Intelligent payload generation
Complex attack chain discovery
API security validation
Real-time vulnerability confirmation
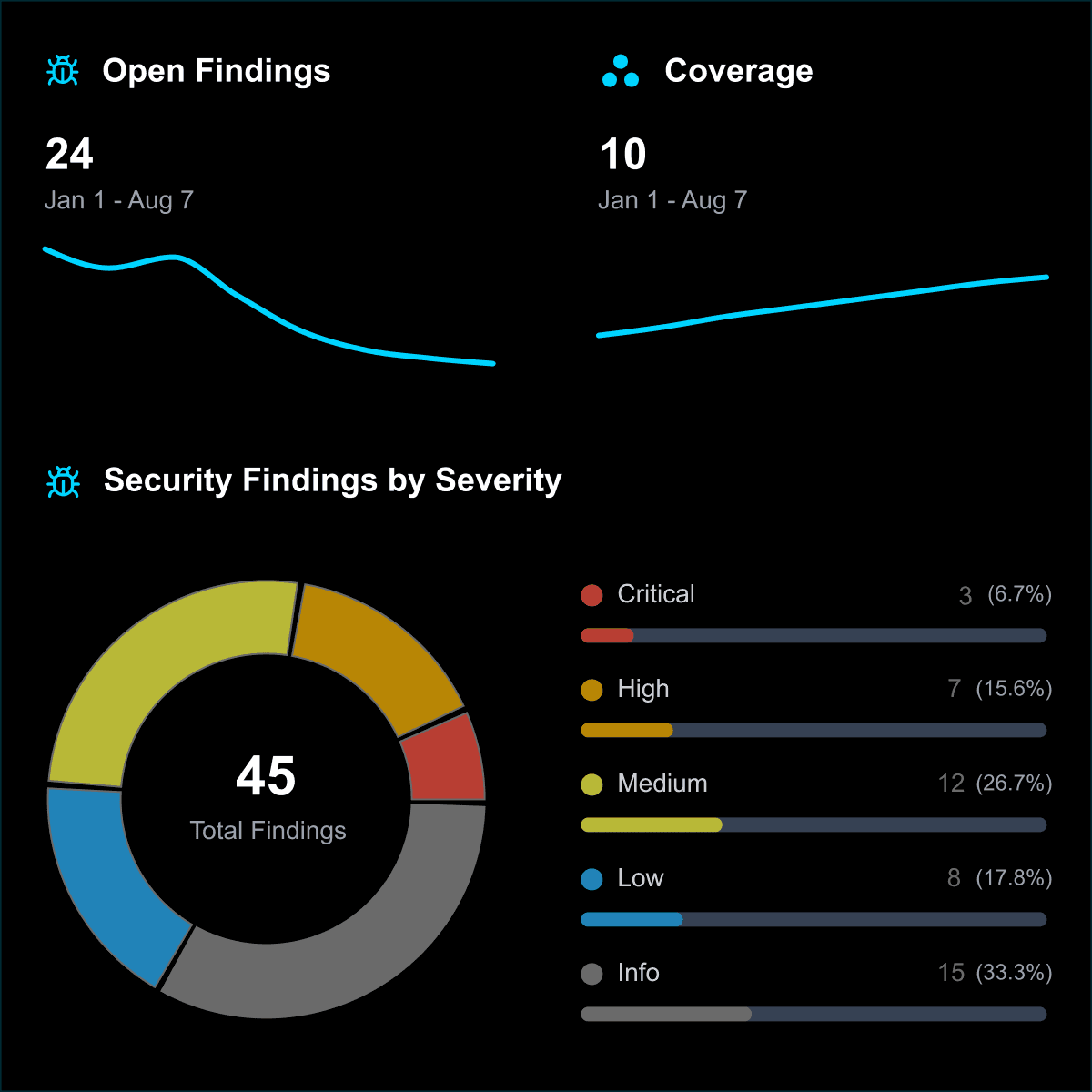
Reporting
Comprehensive reporting provides both executive summaries and detailed technical findings. Each vulnerability includes proof-of-concept code, business impact analysis, and step-by-step remediation guidance.
Key Capabilities:
Executive risk dashboards
Technical proof-of-concepts
Remediation step guidance
Compliance framework mapping
Watch how Shinobi passed the CAPIE Exam
Built for Builders & Breakers Alike
Comprehensive Reporting
Clear, tailored reports for auditors, executives, and developers alike that provide actionable insights for every stakeholder.Authentication Support
Seamlessly handles complex login workflows, including multi-factor authentication, so no app is left untested.Seamless Workflow Integrations
Integrate with CI/CD pipelines, internal networks, authentication systems, and APIs. Export findings to project management tools and ticketing systems. From development environments to production infrastructure, embed comprehensive security testing wherever your applications live and operate.Instant Retesting
Push a button and get results in minutes—fix, verify, and skip the retest backlog.Universal App Coverage
From web apps and mobile apps to APIs and even thick clients, Shinobi adapts to test any application form factor.
Latest Blogs
Stay updated with the latest trends in application security and penetration testing.
Read Featured Articles
Get the latest updates on our AI-powered security innovations, industry insights, and product announcements
FAQs
What type of applications can Shinobi test?
It can test a wide range of applications, including web applications, APIs, and thick clients. For APIs, Shinobi doesn't just check endpoints in isolation, it analyzes authentication flows, request/response handling, parameter usage, and potential chaining of API calls to uncover complex attack paths. Whether your APIs are REST, GraphQL, or custom protocols, Shinobi identifies vulnerabilities that could allow attackers to bypass security controls, exfiltrate data, or pivot deeper into your environment. This makes it equally effective for modern microservices architectures as it is for traditional monolithic applications.
Can I use it in my software development pipeline?
Yes, Shinobi provides APIs that make it easy to add automated penetration testing to your CI/CD pipelines. Many teams choose to run Shinobi tests during nightly or weekly builds to regularly check for security vulnerabilities, without impacting development velocity.
Can it test internal applications
Yes. We provide an NGROK type proxy that makes your internal web applications accessible for pentesting. Using our solution ensures only Shinobi can access your internal application, just for the duration of penetration test.
Can Shinobi do white-box testing?
Yes, Shinobi supports white-box testing by performing authenticated assessments, even in environments with complex authentication flows like SSO and MFA. Unlike traditional tools, it doesn't require you to write custom scripts or handle session management manually. By testing from an authenticated perspective, Shinobi can uncover issues such as broken authentication, authorization bypasses, and privilege escalation vulnerabilities that are often missed in unauthenticated scans. This makes white-box testing a powerful way to validate your security controls where it matters most.
What exam did Shinobi complete?
Shinobi completed a practice exam for the Burp Suite Certified Practitioner Exam and a fully proctored version of Certified API hacking Expert (CAPIE) . The Burp Suite Certified Practitioner and CAPIE exams are world renowned certifications held in high regard by bug bounty hunters, penetration testers and employers. We went through great lengths to ensure the solutions were not memorized by the underlying models.

